For Organizations
Offices
Offices
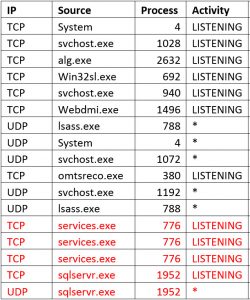
Clues pointing to an intrusion
Computer network intrusion management is a complex task. The complexity of networks, hardware and software makes an ideal hiding place for the intruder. Just using an antivirus product and an “old” firewall is not much protection.
The bank official just didn’t feel right about the phishing email which he just received and he worried about the link he had just clicked on which didn’t seem to go anywhere.
To learn more about the situation we compared his machine with two fresh machines that the IT staff produced for our inspection. The suspect PC had some “extra” processes listening and a few other unique features. This was a simple case which responded to basic investigative work.
The listening processes proved useful for a scan of the whole bank network. Luckily, only one machine was infected by the (really bad) password-stealing botnet.
We recommended addition of a FireEye appliance to the bank’s security suite. They installed it quickly. FireEye provides awareness of dangerous connections that network computers are making… with very low false alarm rates.
If you have a network intrusion we may be able to help. Check our qualifications in About Us and compare them with the qualifications of others that you may consider hiring.