16 Mar Beware of scam emails
Washington state offices have some superstars in cybersecurity. A clear example is the Washington National Guard folks who bring their expertise to state agencies. State officials in the Secretary of State office keep elections secure with airgapped systems and redundant vote checking. Others do a great job.
Not all is good in Olympia, however. Late last month the state auditor’s office made news headlines with a cyber intrusion via a vendor-supplied software package. News reports connect the intrusion with a group in China. On February 23 I detected what appeared to be related nefarious activity. Later a scam email came from what looked like Chase bank. It warned me about suspicious activity on “my” locked account.
Detect intrusions
The purpose of this blog post is to focus on the signs that anyone can observe to foil scammers by detecting their fakery. Here’s a scam email that I received.
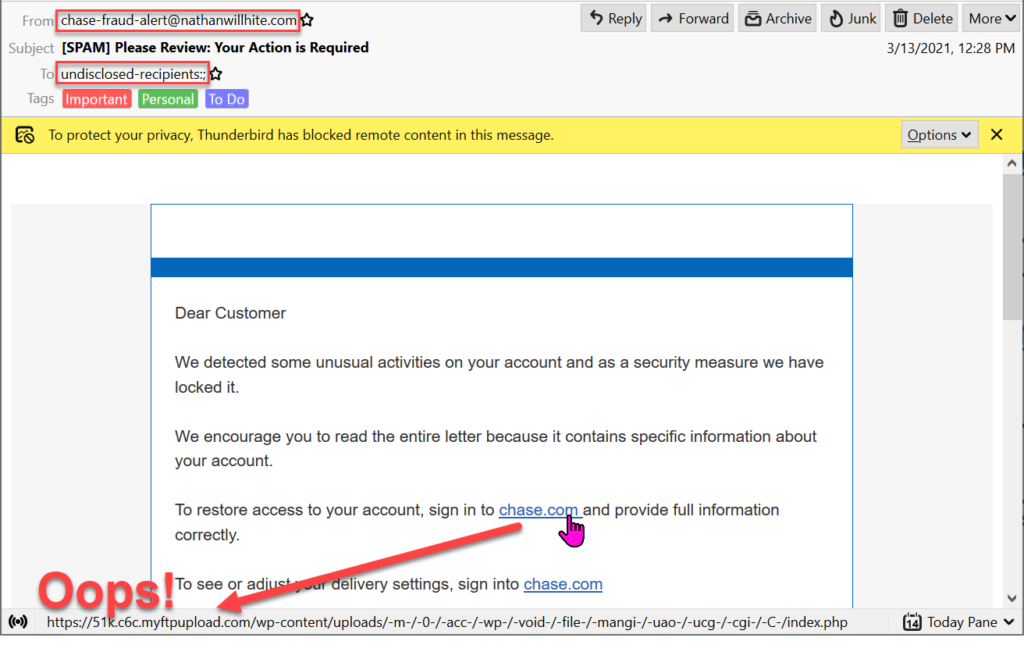
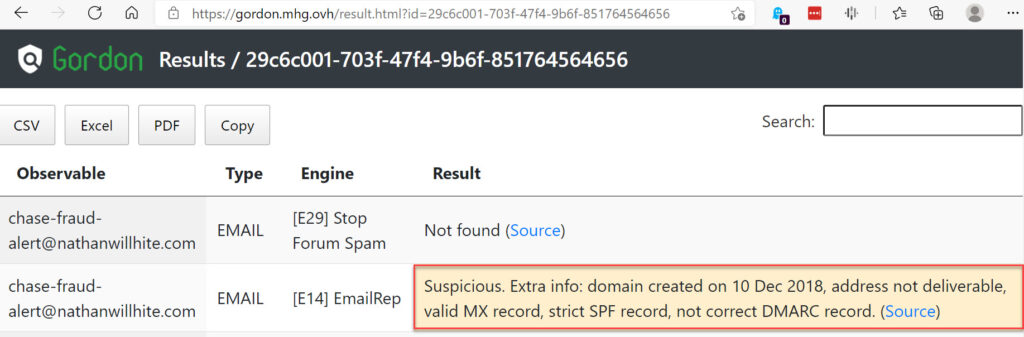
Oddly the email didn’t have a Chase bank sender’s address, but one which gordon.mhg.ovh (now CyberGordon.com) classifies as Suspicious.
Hovering a mouse over the chase.com link in the email one sees that a click would go to a different location. Oops, a scam email!
Use different email addresses for vendors
The email header indicates that it was sent to a (redacted) email address that I have only provided to Washington state offices. Looks like a scam email using personal information from a hack of state servers.
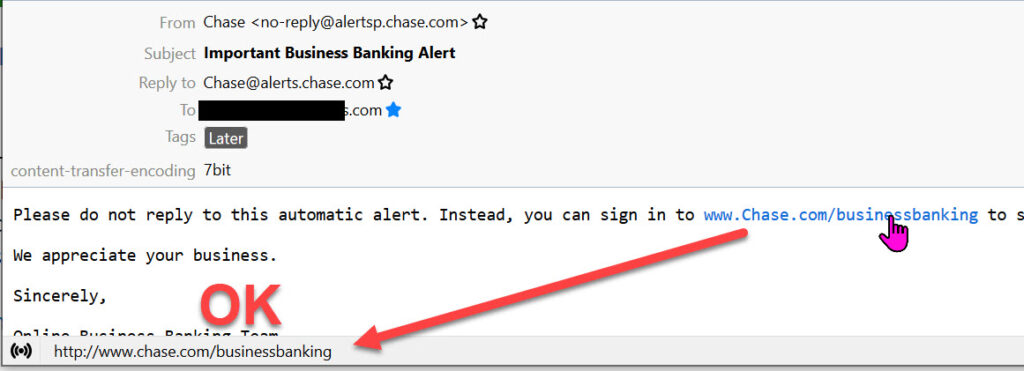
I compare to “real” emails received from chase.com to the (redacted) distinctive email address that I have provided only to Chase bank.
It’s time to call the state and report a likely intrusion. The state offices that I normally deal with use SecureAccess Washington for logins.
When I contacted SecureAccess they gave me a really crazy answer: “We can’t help you; call the department that you deal with”. SecureAccess is the office that I deal with when “securely” connecting to the state. What is really surprising is that a week later the state announced:
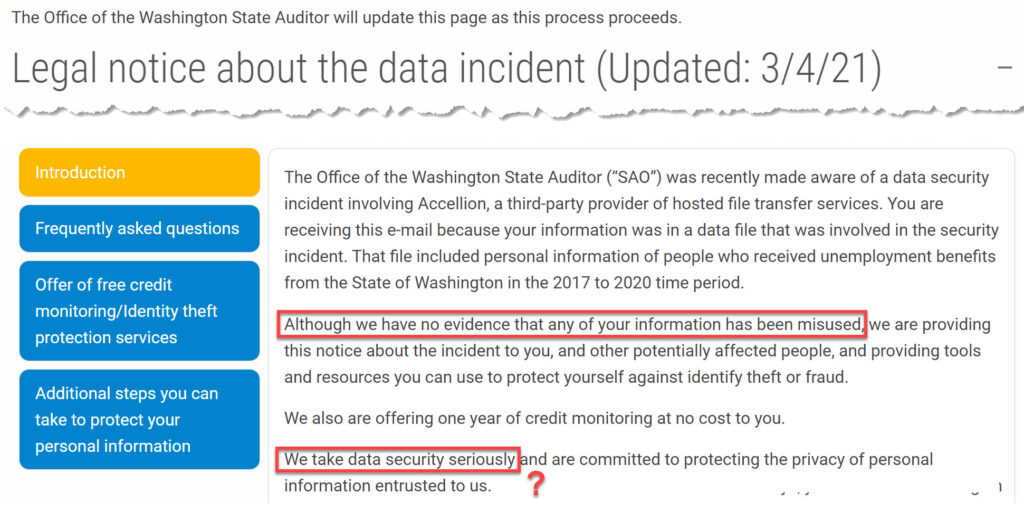
No evidence of information misuse? Do these guys live on a different planet? Those who had received unemployment (a small fraction of the people affected) were sent a letter offering a year of free credit monitoring. It’s hard to understand how credit monitoring would solve the problem.
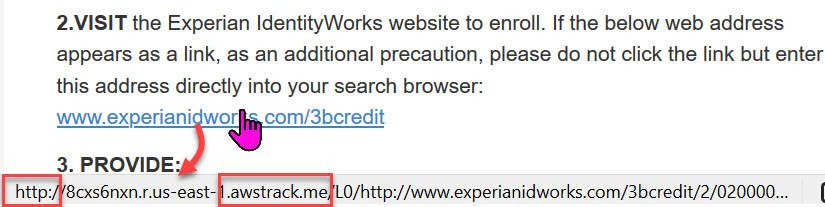
Even this document had logical and security flaws. It would have been more truthful for the state to put out a notice immediately identifying this intrusion. Here’s a suggested announcement.
“Our network has been breached. We have received evidence that citizens’ stolen credentials are being exploited. Be cautious about clicking on links in emails that appear to come from your financial institutions. We are sorry that your private information was vulnerable. Our offer of credit monitoring may be of some value but won’t help if the intruders drain your checking account, you are on your own to defend your assets. For more details check https://esleuth.com/2021/03/16/beware-of-scam-emails/”
Why document these errors?
My purpose is not to embarrass Washington state departments; they have already accomplished that themselves. I hope that this post can clearly:
- Illustrate things that identify scam emails
- Motivate readers to be cautious when receiving “must reply” emails that may be scams
- Present a powerful trick for spotting whose server has been hacked… giving different email addresses to vendors.
- Show that personal cybersecurity can have a big payoff.


