15 May We “WannaCry” about the recent ransomware [Petya update 6/28/17]
WannaCry news
Over the last few days a WannaCry worm/ransomware attack has swept across the planet resulting in headlines. Forensics of the worm which spreads a ransomware payload is being meshed with political news. It’s likely that the key worm concepts came from stolen and leaked US Government cyber tools. Here are some observations from the eSleuth crew.
An early and accurate analysis from Jake Williams of Rendition Infosec was presented in a SANS webinar — on the same day that the attack started! He described the Windows kernel ring-0 (techspeak for serious) mechanism used by a worm to spread the attack in a SANS webcast.
Check out the amount of money received by the most active Bitcoin account currently used by the criminals. As of this blog post the total is only about $20K. The danger of this worm/payload was limited by a security researcher in England who discovered a “kill switch” that stopped spread. Expect that version 2 will not have an easily discovered kill mechanism.
[update] Petya ransomware
It happened all over on 6/27/17 with the release of the “new” Petya ransomware. It has some similarities to Petya which was released a year ago. The new Petya uses the same method as Wannacry to spread damage. Some folks are claiming that this bad actor is actually not being recovered by those paying the ransom. A year ago a workaround was discovered; no news if it works on the current variant.
Currently, the total paid ransom amounts to a very small amount. I guess it’s still a lot of money for a N. K. intruder.
Bottom line: Immediately implementing the following suggestions is important. If you have good offline backups and run a patched version of Windows 10 you will sleep much better.
Our suggestions are:
- Immediately create backups of critical systems and data; store the backups off-network
- This week quit using Windows XP, move to Windows 10
- Patch computer operating systems and applications
- Tighten network security to limit lateral movement by intruders and worms
- If a breach is suspected get help for network forensics and incident response
- Establish a Bitcoin account — your last defense against ransomware
A primary mechanism for spread of the worm is via Windows shares. Check out the stuff that your computer is sharing by typing “net share” at the cmd prompt. One of our machines (that we don’t want to share anything) turned out to have a major share left over from an old backup operation.
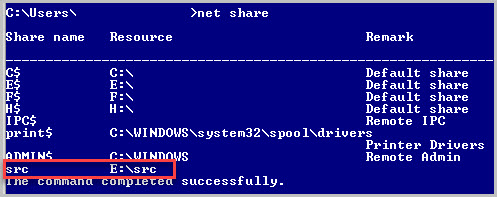
Oops. That shared folder was a big vulnerability that was easily detected.
Defense against WannaCry and many other attacks can be provided by wise network design. A powerful tool is network segmentation. That means putting a layer-7 firewall between the major parts of each network. Workstations should be isolated from others by managed switches. New concepts like Google’s BeyondCorp security approach will help even more to contain attack spreads within a network.
All of these defenses are familiar to security professionals but unlikely to be protecting home or small office networks. When the entire network is at risk it’s time to upgrade security.


